Tips and Tricks for connecting Amazon VPC to CheckPoint Firewall via IPSEC VPN tunnel
One of the services that Amazon Web Services offers that makes it so appealing is “Virtual Private Cloud“. This service allows you to create what is in effect a subnet of your corporate network on Amazon’s cloud, complete with as many VMs as you need. One of the more ambitious configurations is the scenario with multiple subnets on Amazon’s cloud with IPSEC VPN tunnel to your in-house network as well as Internet access. Amazon AWS provides both documentation for configuring edge devices from Cisco, Juniper, and others to set up an IPSEC VPN tunnel to work with Amazon VPC. Amazon AWS also allows you to download a configuration for designed for Cisco devices, Juniper devices, and a few others.
CheckPoint firewalls and edge devices, however, fall into the generic category. Because it falls into the generic category, you cannot download a file with all the relevant commands ready to run as you would with a Cisco or Juniper firewall. With a Checkpoint firewall, you must know both the overview of the network design as well as the minutiae of configuring the hardware. The following are four tips that should help you connect your Checkpoint firewall to amazon VPC via IPSEC VPN tunnel.
1) Do not configure the subnets in your Amazon AWS environment as an IP range in your Checkpoint. Configure them as network ranges. This is because you are connecting the subnet behind your checkpoint to a subnet to a subnet you configured on AWS.
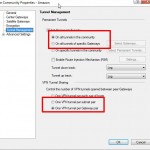
2) Be sure to use one VPN tunnel per gateway pair. Keep in mind that Amazon AWS’s configuration for VPN connections is two tunnels. We set up only one of the two tunnels. We found this adequate for our needs. Your mileage may vary on this one.
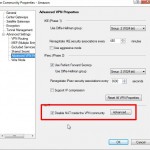
3) Do not enable NAT’ing (Network Address Translation) inside the IPSEC VPN tunnel. The tunnel runs its own NAT’ing inside the link. Both network ranges need to be naked to each other, not NAT’ed. In practice, before turning this on, we found that we could ping from within each network segment to the other side of the VPN tunnel, but not all the way to the other network. After turning this off, our Windows servers inside our network could communicate on all ports with the Amazon EC2 based Windows Server on the other side, and vice versa.
4) Make sure the time on your Checkpoint device is correct. In our working scenario, the Checkpoint firewall was off by 20 minutes. With a disparity like this, there was no way the IPSEC tunnel was going to be usable. The endpoints were building up connections at different advertised times.
Hope these tips help. If they do, please add a comment saying just that.
Thank you,
Commander
Categorised as: IT Services
Leave a Reply